Slow version
Normal version
| Example search term | Use this to find |
|---|---|
System.FileName:~<"notes"
|
Files whose names begin with "notes." The < means "begins with."
|
System.FileName:="quarterly report"
|
Files named "quarterly report." The = means "matches exactly."
|
System.FileName:~="pro"
|
Files whose names contain the word "pro"
or the characters pro as part of another word (such as "process" or
"procedure"). The ~= means "contains."
|
System.Kind:<> picture
|
Files that aren't pictures. The <> means "is not."
|
System.DateModified:05/25/2010
|
Files that were modified on that date. You can also type
"System.DateModified:2010" to find files changed at any time during
that year.
|
System.Author:~!"herb"
|
Files whose authors don't have "herb" in their name. The ~! means "doesn't contain."
|
System.Keywords:"sunset"
|
Files that are tagged with the word sunset.
|
System.Size: <1mb |
Files that are less than 1 MB in size.
|
System.Size: > 1gb |
Files that are more than 1 GB in size.
|
*#9900#







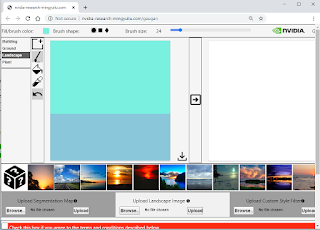
NVIDIA's GauGAN AI Machine Learning Tool creates photorealistic images from Simple Hand Doodling http://nvidia-research-mingyuliu.com/...